Security
IoT systems have many security issues in common with other technical domains such as Web or mobile applications. In addition, there are some security issues that are mainly or exclusively relevant to IoT.
Figure 1 summarises the meaning of some common security terms and their relationships. The process shown on the left can be interpreted as the one that the threat actor uses to compromise a system; however, evaluating the security weaknesses of a system requires the analyst to think like the threat actor. The process shown is therefore equally applicable to the analyst.
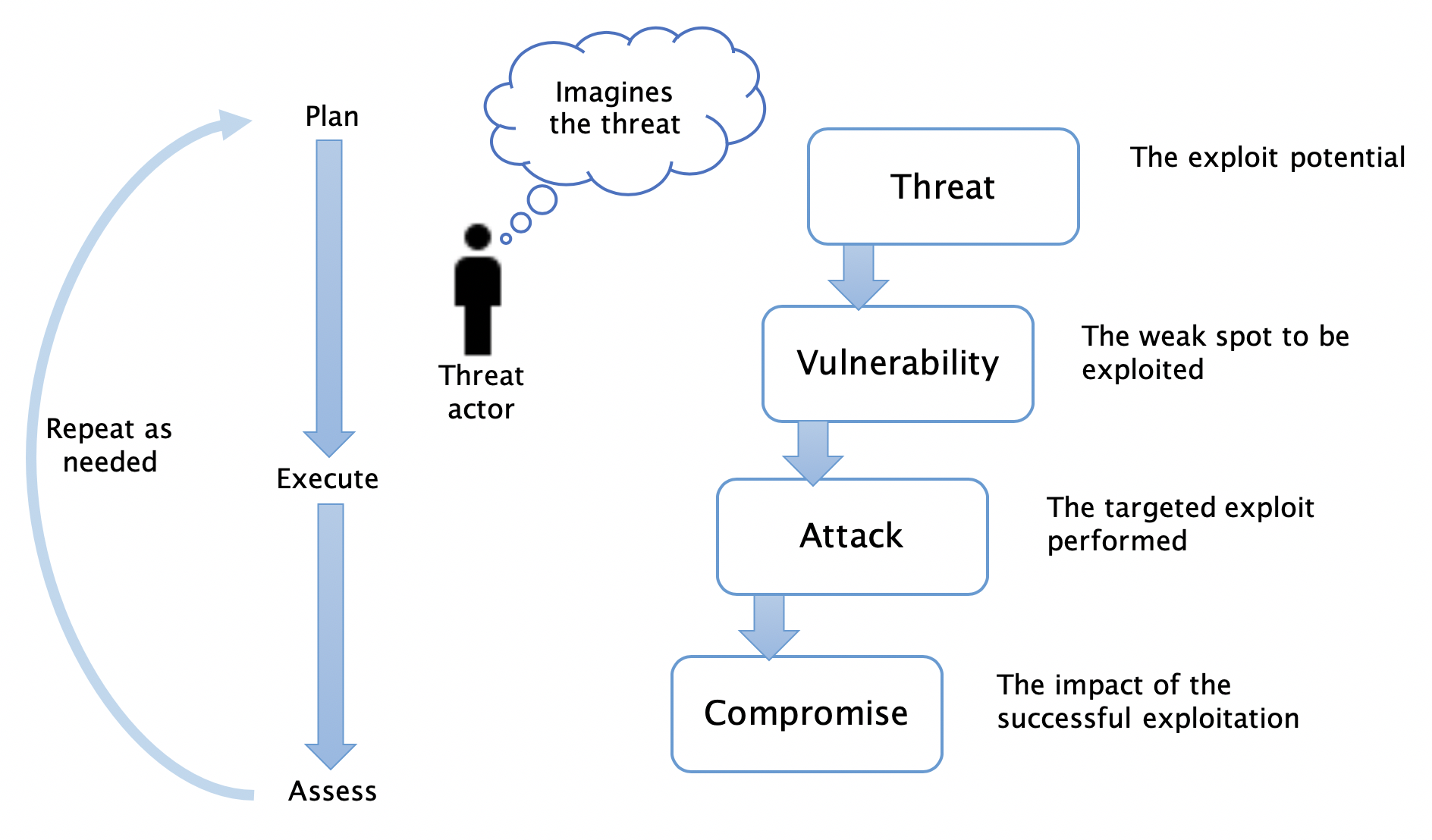 Figure 1: Security concepts (Russell & Van Duren, 2018)
Figure 1: Security concepts (Russell & Van Duren, 2018)
Some of the most relevant types of attack for IoT are:
- Wired and wireless scanning and mapping attacks
- Protocol attacks
- Eavesdropping attacks (loss of confidentiality)
- Cryptographic algorithm and key management attacks
- Spoofing and masquerading (authentication attacks)
- Operating system and application integrity attacks
- Denial of service and jamming
- Physical security attacks (for example, tampering and interface exposures)
- Access control attacks (privilege escalation)
For a full discussion of each of these, please refer to Russell & Van Duren (2018). The remainder of these notes will concentrate on the threat modeling process.