Introduction
IoT
Much hyped and rapidly growing, the Internet of Things (IoT) is increasingly becoming a part of our daily lives.
At its core IoT is built on sensors reading data; temperature, light level, humidity etc. and transmitting those small pieces of information over a gateway to a network.
The first IoT device created at Carnegie Mellon in the late 1900's (Circa 1981) monitored the indicator lights of a coke machine to determine if coke was in stock. The information was sent to a gateway which was connected to the ARPANET and anyone with a working connection could find out if there were cokes in the machine or not.
Today there are a myriad of devices connected to the internet and each other, sharing data about their environment, forwarding it over networks to applications through which we can interact and control them.
The smart home is an excellent example of IoT interoperability over a local area network (LAN). End-devices such as smart locks, lighting systems and heating controls all connected via Wi-Fi and operating on mains power.
But IoT isn’t restricted to the home and has wider applications in transportation, building management and cattle tracking, to name just a few.
Operating in these environments places competing demands on the technology. We need these IoT end-devices to be operational for a long period of time, using only battery power and transmitting a great distance.
Simultaneously we are limiting the transmission power available and demanding long-distance transmissions. How do we get around this problem?
LoRa
As stated, end-devices read and transmit small pieces of data (generally), so although we cannot increase the transmission power, we can still achieve a wide area network (WAN) with low power, if we decrease the bandwidth used.
LoRa (Long Range) is a radio frequency modulation which achieves this utilising CSS (Chirp Spread Spectrum), it is the physical layer of the network technology. LoRa is an internationally accepted standard in the creation of Low Power Wide Area Networks (LPWAN), and operates worldwide on the unlicensed ISM (Industry, Science and Medical) radio band.
This modulation technique allows for long-range transmission of small packets up to three miles in an urban environment and ten miles in a rural environment. It is resistant to interference and offers a low 'bit error rate' (BER).
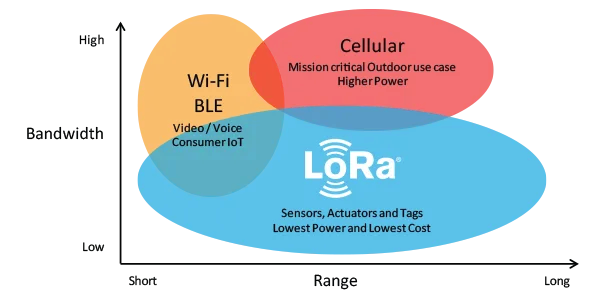
LoRa is ideal for IoT devices such as sensors, actuators and other devices which transmit and receive small packets of data at low bit rates.
CSS Chirp Spread Spectrum
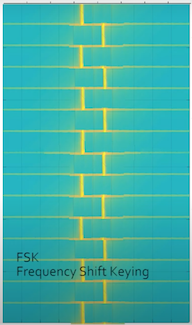
FSK (Frequency Shift Keying) is a digital modulation of a carrier signal which uses two frequencies representing binary 1’s and 0’s, to transmit data.
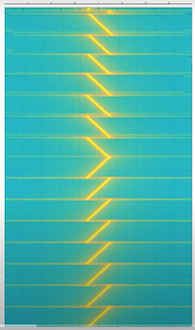
CSS (Chirp Spread Spectrum) rather than jumping from one to the other, sweeps between frequencies with rising and falling (up and down) signals. This signal is more complex and resilient to interference.
Signals can be altered by the speed of the sweep, known as the sweep rate, or spreading factor (SF), and the range over which they sweep, the bandwidth.
Greater bandwidth provides a better signal (EU restrictions) but bandwidth is restricted.
Faster sweep rates allow for the transmission of more data but are harder to resolve and decode than a slower sweep rate.
Generally, if an End-Device is close to a gateway it can use a higher spreading factor and a lower bandwidth. Devices which are located further away would need to find a balance of lower spreading factors and higher bandwidths for reliable communication.
LoRaWAN

The word 'LoRa' is often used as a catchall term to describe devices, gateways and networks. It is also confused with LoRaWAN which it is not.
Specifically, LoRaWAN represents the MAC layer of the network technology. It defines how devices use the LoRa hardware and controls mechanisms for transmission such as ADR (Adaptive Data Rate).
To connect IoT devices to other devices and applications requires LoRaWAN.
LoRaWAN handles
- Security features
- Activating devices on a network
- Frame counting
- Acknowledging messages
- Synchronising data sending windows
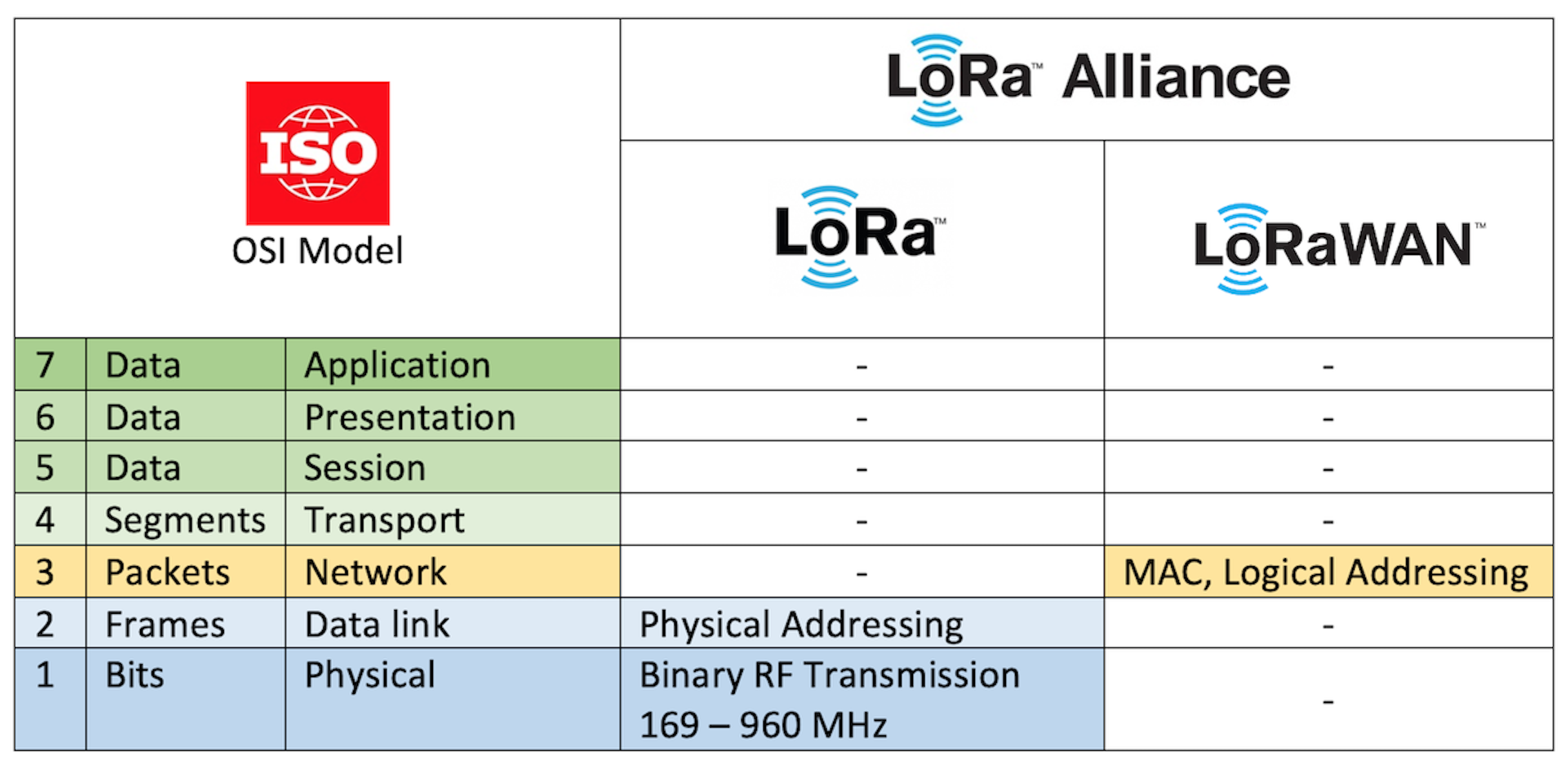 LoRa and LoRaWAN as they pertain to the OSI layer model
LoRa and LoRaWAN as they pertain to the OSI layer model
The protocol is developed and maintained by The LoRa Alliance and (at the time of writing) the current version is 1.0.4
Network Architecture
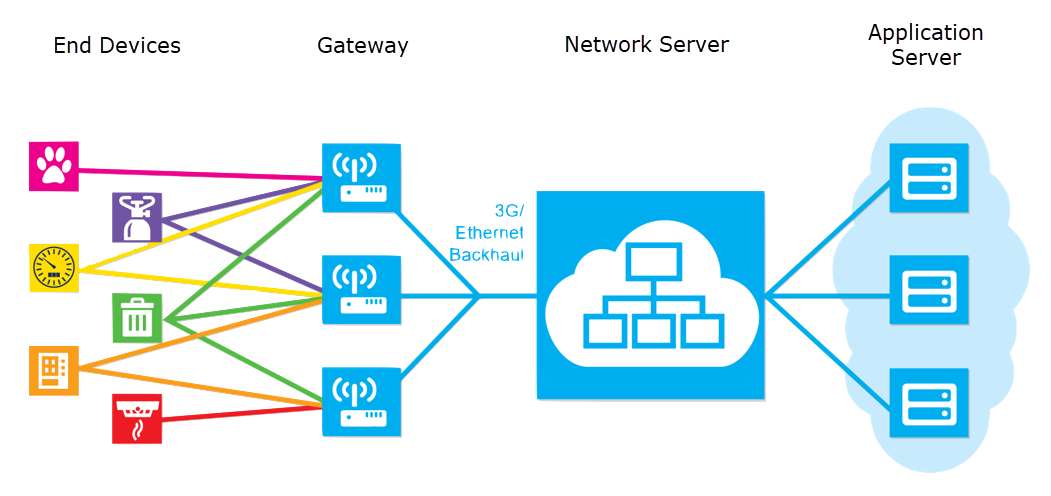
A LoRa network consists of several elements:
-
Topography: End- devices are typically in a star-of-stars topology with gateways forming a transparent bridge. These relay messages between end-devices and a central network server in the backend.
-
End-devices: These are the elements of the network where the sensing or control is undertaken. Normally remotely located.
-
LoRa gateway : The gateway receives communications from end-devices and transfers them onto the backhaul system. The backhaul can have an Ethernet, cellular or other wireless connection. Gateways connect to the network server using standard IP connections.
-
LoRa Network Server: The network server manages the network, it acts to eliminate duplicate packets, schedules acknowledgement, and adapts data rates.
-
Remote computer: With the above elements in place a remote computer can then control the actions of the endpoints or collect data from them - the LoRa network being almost transparent.
Communication with end-devices is generally bi-directional, but multicast operation is also possible, which is useful for features such as software upgrades.
It should be noted that a gateway can listen to multiple channels at once, while an end-device can only listen on one channel at a time.
End-devices
As stated, there are a myriad of devices generating, receiving, and transmitting data through networked components. But different applications of the technology have different requirements and not all LoRaWAN end-devices are created equally.
 Temperature and humidity sensors
Temperature and humidity sensors
-
Sensors share data with other network components, such as gateways, base stations, and servers, for further processing. These devices consume very little power as they transmit tiny data packets and do not synthesize information natively.
Because of their low energy demands and ability to transmit information over long distances, wireless sensors are ideal for IoT applications that deal in very small data payloads.
-
Actuators are devices that take communication signals and convert them into mechanical action. Examples of actuators include electric car door locks, electric motors, and comb drives.
As end-devices in wireless sensor networks, actuators can easily take data inputs from surrounding environments and cause a mechanical response in another piece of equipment. Actuators can be valuable in LoRaWAN applications involving industrial activity and processes.
End-devices are divided by class defining their communication method. Actuators must be Class C devices, meaning they can receive data inputs at anytime. Class C actuators are always on, whereas Class A devices (i.e. wireless sensors) must “wake up” in order to send an uplink before they can receive data.
Class A - bi-directional end-devices:
LoRaWAN class A endpoint devices provide bidirectional communications. To achieve this, each endpoint transmission is followed by two short downlink receive windows. The transmission slot scheduled by the particular endpoint is based upon the needs of the end point and also there is a small variation determined using a random time basis.
LoRa Class A operation provides the lowest power option for end points that only require downlink communication from the server shortly after the end-device has sent an uplink transmission. Downlink communications from the server at any other time wait until the next scheduled uplink time.
Class B - bi-directional end-devices with scheduled receive slots:
LoRa Class B devices provide the Class A functionality and in addition to this they open extra receive windows at scheduled times. To achieve the required synchronisation from the network, the endpoint receives a time synchronized Beacon from the gateway. This allows the server to know when the end-device is listening.
Class C - bi-directional end-devices with maximal receive slots:
LoRa Class C devices provide nearly continuously open receive windows. They only close when the endpoint is transmitting. This type of endpoint is suitable where large amounts of data are needed to be received rather than transmitted.
Security
The physical layer, LoRa, doesn’t provide any security measures it only provides a check sum. Security is managed by LoRaWAN using the three pillars of security.
- Authenticity - Knowing with which device you are communicating with.
- Integrity - Knowing that the data has not been tampered with by intermediate party.
- Confidentiality - Encrypted data.
On the Network layer a Unique Network Session key (EUI64) ensures Integrity and Authenticity, and on the Application layer an Application Session key ensures confidentiality. Both are AES 128-bit keys, meeting the industry standard for securing communications.
Employing these layers of encryption ensures that the LoRa network remains sufficiently secure.
Establishing a LoRaWAN session
There are two methods of establishing a LoRaWAN session. Over The Air Authentication (OTAA) and Authentication By Personalisation (ABP). Both methods have their place, deciding which to use is a balance of security with resource constraints.
Dynamically joining a network – OTAA
- Sends join request
- Any network server can respond
- Security keys generated at each activation
OTAA is the recommended method of establishing a LoRaWAN session as a new session is created with each join and keys are re-keyed with each join.
Hard coded session – ABP
- No need for a join procedure
- Dev addr and security keys hardcoded into device
- More efficient
- Not as secure
ABP provides a fixed session with no join procedure. Security keys stored in persistent memory. Devices can only join a preconfigured network.
Attributes of LoRaWAN Networks
- LoRaWAN end-devices are optimized to operate in low power mode.
- LoRaWAN devices can transmit and receive signals over a considerable distance.
- LoRaWAN networks provide deep indoor coverage.
- No license fees to deploy a LoRaWAN network.
- LoRaWAN Network Servers have high capacity, handling millions of messages from thousands of gateways.
- LoRaWAN ensures secure communication using AES-128 encryption.
- Remote firmware updates are supported, for a single end-device or a group of end-devices.
- A LoRaWAN network can geolocate end-devices using triangulation without the need for GPS.
- LoRaWAN end-devices can perform seamless handovers from one network to another (OTAA).
- Minimal infrastructure, low-cost end nodes and open source software.